Technology
Gmail Mail Attachment Size Limit: Best Understanding Its Restrictions and Workarounds 2024
Gmail mail attachment size limit in today’s digital age, email is an essential tool for communication, whether for professional, personal, or educational purposes. As one of the most popular email services globally, Gmail provides a wide range of features to streamline user experience, including the ability to send and receive attachments. However, Gmail users often […]
SMTP Office 365 Settings: A Comprehensive Guide
SMTP office 365 settings in the modern era of business communication, email is an essential tool that plays a critical role in day-to-day operations. For organizations using Office 365, understanding how to configure Simple Mail Transfer Protocol (SMTP) settings can enhance email management, improve security, and optimize mail delivery. In this comprehensive guide, we will […]
Configuring SMTP Settings Office 365: A Comprehensive Guide
SMTP settings office 365 in today’s digital age, email remains a crucial tool for communication. Whether it’s for personal or business use, ensuring that emails are sent and received reliably is a top priority. Microsoft SMTP settings office 365 (now known as Microsoft 365) is a popular platform for managing emails due to its wide […]
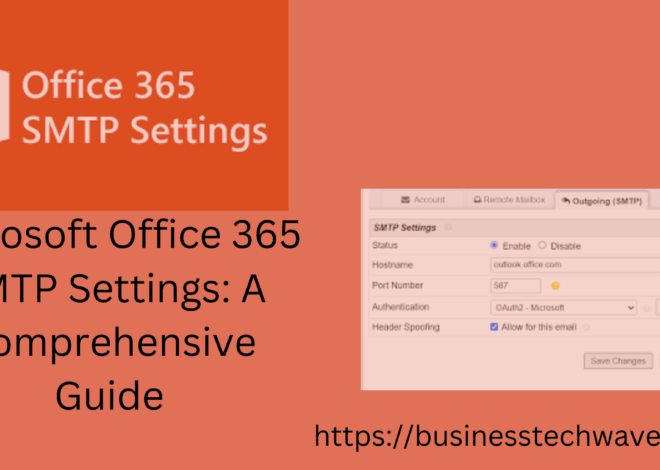
Microsoft o365 SMTP Settings: A Comprehensive Guide
Microsoft o365 SMTP settings has become one of the most popular and versatile platforms for business communication. It offers a comprehensive set of tools and services, including email through Exchange Online, which is built into the O365 platform. If you’re managing emails and need to configure SMTP (Simple Mail Transfer Protocol) settings to send or […]
Validating Email: Best Practices and Importance 2024
Validating email in the digital age, email remains one of the most common methods of communication, both for personal use and business operations. It is the cornerstone of marketing campaigns, customer service, and registration systems for countless platforms. However, ensuring the validity of email addresses is essential to the smooth functioning of these systems. Validating […]
Understanding Mail Exchanger MX Records: A Comprehensive Guide 2024
Mail exchanger mx records communication is the backbone of modern businesses, organizations, and personal interactions. From basic messages to sophisticated marketing campaigns, email services ensure quick, reliable, and secure information exchange. Behind this seamless interaction is a hidden technical infrastructure that makes it all possible, and at the heart of email delivery lies an essential […]
Network Secure: Best Protecting Digital Infrastructures 2024
Network secure in today’s digital age, networks serve as the backbone of communication, business operations, and data transmission. The rapid expansion of interconnected devices, cloud services, and the Internet of Things (IoT) has created both tremendous opportunities and significant risks. As cyber threats grow in sophistication and scale, network security has become a top priority […]
Mail Exchange Lookup: A Comprehensive Guide to Understanding MX Records 2024
Introduction Mail exchange lookup in today’s world, email is a critical communication tool for both personal and business purposes. Every day, billions of emails traverse the internet, reaching inboxes all over the world. But have you ever wondered how an email knows where to go? This is where Mail Exchange (MX) records come into play. […]
Understanding MX Server Lookup: A Comprehensive Guide 2024
MX server lookup email communication is an integral part of modern business, and for any organization, the reliability and efficiency of email systems are critical. At the heart of email communication lies the Domain Name System (DNS), a cornerstone of internet architecture that enables users to send emails to specific domains. One key component of […]
How do You Block Spam Emails: A Comprehensive Guide 2024
How do you block spam emails are an ever-present nuisance in our digital lives. These unsolicited messages can range from annoying advertisements to dangerous phishing attempts, making effective spam management essential for maintaining a secure and efficient inbox. This guide will explore how do you block spam emails various strategies, focusing on both preventive measures […]